
-
Apexlink
Real Estate
-
DLS
General Insurance
-
DMV
Government
-
Entiger
Fintech
-
GIS Mapping
Gas & Petroleum
-
HMS
Employee Benefit
-
HAWA
Government
-
Harley
Community
-
IHG
Hotel & Tourism
-
Sparkseeker
Humane Tech
-
Track Ninja
Sports
-
Response Vision
Disaster Management
- AI/ML Services
- Application Services
- Automation Services
- Cyber Security
- Chatbot Experts
- Data Analysis
- Data Warehouse Services
- Digital Commerce Services
- Digital Transformation
- Infrastructure Service
- Low Code/No Code
- Managed IT Services
- IT Support
- IT Consulting
- IT Outsourcing
- Mobile App Development
- IOS Development
- Android Development
- Cross Platform Development
- Gaming App Development
- Software Development
- System Design & Architecture
- Testing Services
- Web Development
Accelerators
POCs and Products
Ransomware crews now weaponize generative AI to write polymorphic malware in minutes, while hybrid work has dissolved every neat network perimeter. Traditional “castle-and-moat” defenses, and even first-generation Zero Trust rollouts that rely on static rules struggle to keep pace. The result is a widening protection gap: 90% of companies admit their defenses can’t counter today’s AI-enabled threats, and 77% lack the data and AI security practices to close it.
That gap is fueling a second wave of Zero Trust, one where artificial intelligence continuously analyzes context, adapts policies, and responds autonomously.
Zero Trust 101 and Why the First Wave Hit a Wall
Zero Trust architecture (ZTA) starts with a simple principle: “Never trust, always verify.” Every request is explicitly authenticated, authorized and encrypted, yet early adopters ran into three obstacles:
Volume of signals – Millions of identities, devices and workloads create more telemetry than human analysts can interpret.
Static policies – Rule sets become outdated the moment the threat landscape shifts.
Operational drag – Rigid controls slow productivity, spawning user workarounds that re-open risk.
No surprise that Gartner predicts 30% of organizations will abandon Zero Trust projects by 2028 unless complexity is reduced and automation added.
What Is AI-Driven Zero Trust?
AI-driven Zero Trust fuses core ZTA controls with machine-learning models that:
- Detect anomalies in real time across identity, endpoint, network and cloud telemetry.
- Score risk continuously and adjust permissions (Just-in-Time / Just-Enough-Access).
- Trigger automated playbooks to isolate hosts, revoke tokens or force re-authentication in milliseconds.
In effect, AI supplies the contextual intelligence and speed that first-generation Zero Trust lacked.

How AI Enhances Zero Trust Architecture
| Capability | Traditional ZTA | AI-Driven ZTA |
| User & device verification | Static MFA checks | Behavioural analytics and device-posture scoring for adaptive access |
| Policy enforcement | Rule-based segmentation | Dynamic micro-segmentation that rewrites rules on risk signals |
| Intelligent threat detection | Signature / log correlation | Predictive anomaly detection on live telemetry |
| Response | Human-triggered | Autonomous containment & remediation |
Key enablers include:
Behavior Analytics – Models build baselines and surface outliers such as a CFO logging in from an unknown IP at 3 a.m.
Predictive Risk Scoring – Continual scoring lets policies flex rather than force a blanket deny.
Automated Response – Endpoint AI can cut mean-time-to-respond (MTTR) by 55% and lower incident likelihood by 60%.
Business Benefits of Implementing AI-Driven Zero Trust
The following benefits highlight why businesses need AI in security.
Higher Efficacy
63% faster threat detection and 338% ROI reported by enterprises using AI-powered security platforms.
Scalability for Cloud & Hybrid
84% of organizations now pursue Zero Trust specifically for cloud workloads.
User Experience Gains
Predictive, context-aware access cuts friction, ending the “security vs productivity” trade-off.
Regulatory Readiness
Continuous verification and granular logging simplify evidence collection for frameworks like HIPAA, PCI DSS 4.0 and NIS2.
Futureproofing
AI models update automatically with new threat intel, protecting investments as adversaries evolve.
Anatomy of an AI-Powered Zero Trust Architecture
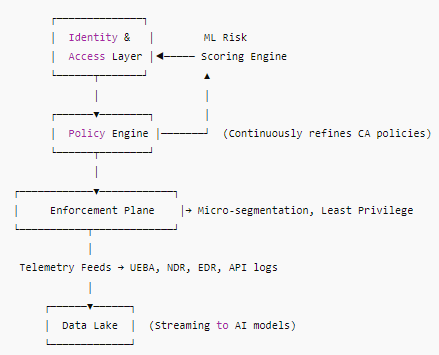
Use-Case Snapshots
Healthcare
AI flags anomalous data exfiltration attempts from a medical device network and auto-isolates the segment, protecting ePHI.
Financial Services
Zero Trust security with real-time AI analytics thwarts credential-stuffing attacks against customer portals without blocking legitimate high-volume traders.
Manufacturing OT
AI-powered micro-segmentation prevents lateral movement from compromised PLCs to ERP systems.
Remote Workforce
Risk-adaptive authentication tightens or loosens controls based on location, device health and user behavior.
Implementation Roadmap for Enterprises
1. Baseline & Prioritize – Map identities, data flows and “protect surfaces”. Conduct a maturity assessment.
2. Unify Telemetry – Feed identity, endpoint, network and cloud logs into a scalable data lake/SIEM.
3. Pilot AI Analytics – Start with UEBA or XDR modules that offer pre-trained models. Measure detection lift and MTTR.
4. Automate Response – Integrate SOAR playbooks for quarantine, credential revocation and ticket enrichment.
5. Iterate Policies – Use model insights to refine least-privilege roles and micro-segments.
6. Measure & Report – Track KPIs such as risk score reduction, false positives, dwell time and user experience scores.
Challenges & Mitigations
- Model Drift & Bias – Schedule regular model retraining and validations against new threat feeds.
- Data Quality – Normalize and de-duplicate logs before feeding them into AI engines to enhance the performance of AI services and ensure accurate, reliable insights.
- Skill Gaps – Upskill SOC analysts on data science fundamentals; leverage MSSPs for managed detection.
- Vendor Lock-In – Prefer open standards (OCSF, MITRE ATT&CK, NIST 800-207) to enable tool interoperability.
- Privacy & Ethics – Apply differential privacy and strict data retention to comply with GDPR and emerging AI regulations.
Future Trends: Toward Autonomous, Self-Healing Security
Autonomous Workspaces
Self-configuring environments implement predictive Zero Trust at the UX layer.
Network-As-A-Service Zero Trust
Built-in, behavioral AI at the fabric level removes bolt-on complexity.
Generative AI for Adversary Simulation
LLMs craft sophisticated red-team attacks, pushing blue teams to automate countermoves.
Post-Quantum Readiness
AI helps prioritize cryptographic migration paths based on asset criticality.
Why Partner with Seasia Infotech for AI-Powered Security Solutions
Seasia’s Cybersecurity Center of Excellence combines deep Zero Trust expertise with advanced AI/ML solutions capabilities. Our team offers:
- Integrate UEBA, XDR and SASE platforms into cohesive Zero Trust architectures.
- Develop custom ML models for sector-specific anomaly detection.
- Automate incident response through SOAR playbooks and infrastructure-as-code.
- Ensure compliance with HIPAA, PCI DSS 4.0, GDPR and NIS2, leveraging our global regulatory practice.
Whether you’re starting your Zero Trust journey or scaling across multi-cloud/hybrid estates, Seasia delivers AI-powered cybersecurity solutions that protect, adapt and evolve.
Frequently Asked Questions
Q1. What makes AI-driven Zero Trust the future of cybersecurity?
Continuous, AI-powered verification eliminates blind spots and adapts to evolving threats faster than static controls.
Q2. How does AI enhance Zero Trust architecture?
It provides behavioral analytics, risk-adaptive access and automated response, turning policy from static to dynamic.
Q3. Is AI-powered Zero Trust scalable for hybrid environments?
Yes, cloud-native analytics and SASE frameworks push uniform policy enforcement to any user, device or workload.
Q4. Can AI stop data breaches in real time?
AI can detect anomalies within seconds and trigger immediate containment actions, drastically reducing breach impact.
Q5. What are the first steps to adopt AI-driven Zero Trust?
Begin with a readiness assessment, consolidate telemetry, and pilot an AI-enabled UEBA or XDR solution before full rollout.








 Blockchain
Blockchain Cloud Computing
Cloud Computing Infrastructure
Services
Infrastructure
Services Metaverse
Metaverse QA
Automation
QA
Automation UI/UX
UI/UX







